Agile and Security
-
Simone Rossi
- 20 Jun, 2024
- 02 Mins read

We have just completed the web security program "Build IT right, have a night", and you may wonder how Agile practices can be used to enhance the security of an application...
Well, that's not obvious! Although we may be building software using an Agile approach, we are still bound to the traditional security approach. Unfortunately, it goes hand in hand with a "waterfall" project management technique
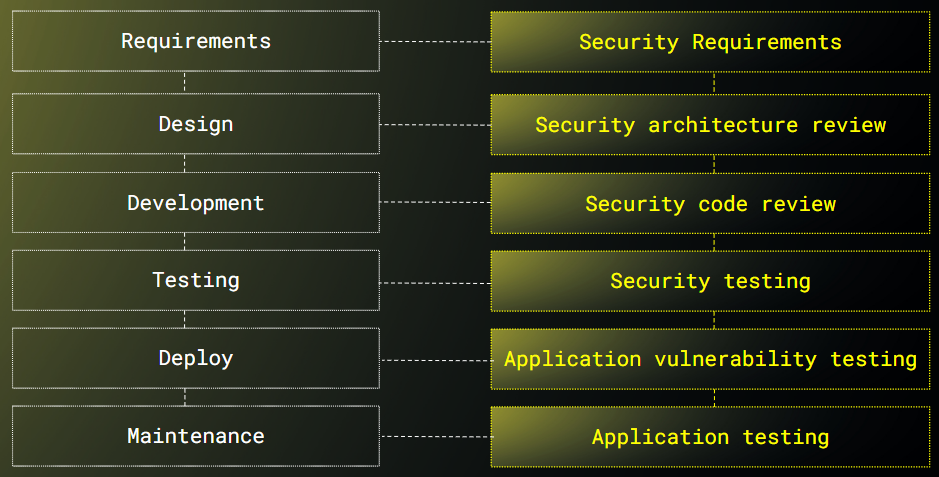
And basically what we do is to deliver business features using an Agile approach (iteratively and incrementally), and then - right before going to production - we ask our security experts to assess our application and... BOOM! We find out that we need three or four more weeks to repair security issues :(
So if we wanted to shift security left, where can we operate? Of course in the product backlog: the primary resource of features! There are two different approaches, and both of them can be used: include security requirements inside user stories, and use what are so called "evil user stories"
Expanded user stories
Imagine that you as product owner are writing a user story for a user registration. It may be as simple as
"As a user, I want to be able to set my username and password to register to the application"
But if you want to include security requirements, you could add the following - as tasks or as acceptance criteria:
As a user, I want my account credentials to be created, stored and transported securely so that they can’t be guessed, intercepted or reused by an attacker
As a user, I need the application to allow passphrases and/or difficult passwords
As a user, I need password entry and other fields containing sensitive information to disallow caching, or auto-complete
Evil user stories
Imagine being a malicious user instead of a nice and happy one. Evil user stories describe how an attacker might exploit the application, and believe me, behind every user story there is always one or more evil user story as well! As example, for the user story:
As a customer, I want to select products, and add them to my shopping cart so that I can buy them
we may have these evil stories:
As an** evil user**, I want to manipulate requests to change prices when I add products to the shopping cart
As a disgruntled employee, I want to show all items are out of stock so that the company is unable to generate revenue
As you can see, we may have many different types of bad users, not just hackers that want to steal our credit card data!
Product owner and security people
We all know that the person having the responsibility to maintain the product backlog is the product owner. However (s)he can be helped by other people to do so. What I mean is that the product owner does not need to know in depth all security requirements, all security issues etc... (S)he can ask for help to security people, or brainstorm evil user stories with all the developers (believe me, these are very fun sessions!)